Jun 25, 2013 | General Articles, Reviews
I’d like to share a handy dandy online tool that I discovered a few years ago while running my IT consulting business. While it’s not the One Marketing Tool to Rule Them All, it’s a great starting point by providing a bird’s eye view of where you stand in relation to other websites (including your competition!).
Jun 24, 2013 | HowTo, Technology
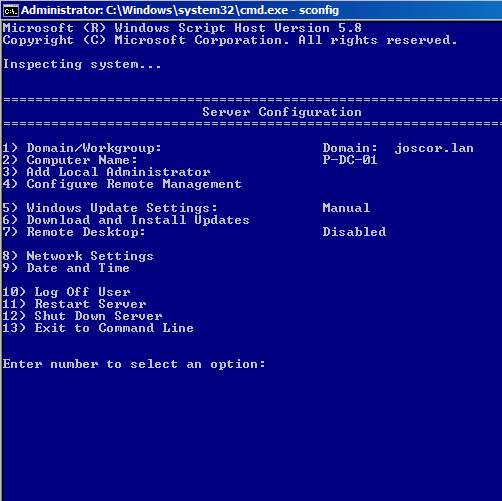
“In Windows Server 2008 R2, in addition to the Dism.exe command, you can use the Server Configuration tool (Sconfig.cmd) to configure and manage several common aspects of Server Core installations”. This article will give a brief overview of SConfig as well as a quick tutorial on using this handy tool to install Windows Updates on your Windows Server 2008 R2 Core server.

Jun 24, 2013 | HowTo, Technology
The Microsoft Remote Server Administration Tools (RSAT) package allows administrators to utilize the Microsoft Management Console (MMC) to manage Windows Servers remotely. These tools become incredibly useful when working with Microsoft Server 2008 R2 Core servers as they do not provide a GUI for tasks such as Active Directory management or DNS/DHCP management.

Jun 23, 2013 | General Articles
In the workforce, land grabbing refers to an employee or department that excessively volunteers or forces their way to acquiring company projects or tasks, creating an uneven distribution of projects. This article explains why employees/departments do this and how employers can minimize this behavior.

Jun 20, 2013 | Technology, WWPass related
OpenVPN relies on cryptographic keys and certificates for secure communication between a VPN client and the remote server. The WWPass PassKey technology, in conjunction with Microsoft CryptoAPI, can fortify those keys and give users and systems administrators peace of mind by taking the challenge of protecting private cryptographic information out of their hands.





