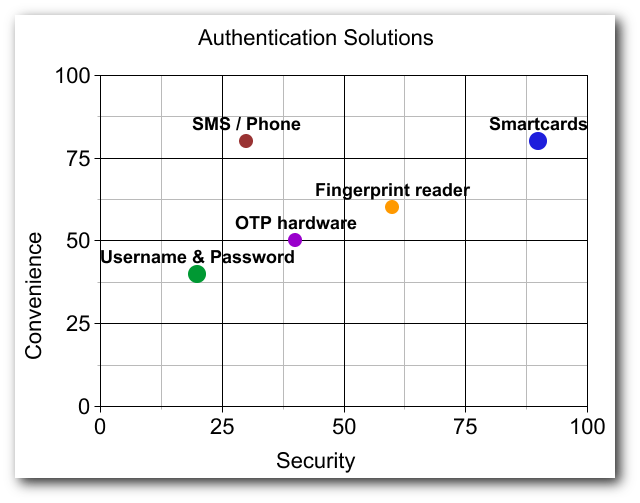
Authentication solutions comparison
There’s a lot of debate in the information security industry about what the next-gen solution will be for authenticating users into services (websites, applications, etc…). I’ve collected a list of suggested authentication solutions (both hardware and software mechanisms) and will try to shed some light on their pros and cons.
