There’s a lot of debate in the information security industry about what the next-gen solution will be for authenticating users into services (websites, applications, etc…). I’ve collected a list of suggested authentication solutions (both hardware and software mechanisms) and will try to shed some light on their pros and cons. This is by no means a definitive list or even a comprehensive list of all authentication schemes. This article attempts to touch on the most frequently discussed methods of which I’m aware. I’ve also made a point to focus on solutions that are not horribly expensive (cost prohibitive to average consumers) nor “enterprise-focused” which would require either too much money (once again, cost prohibitive) or have complex network requirements (which would not be found in an average consumers home). Finally, a disclaimer; I work for WWPass Corporation, a manufacturer of secure authentication smartcards but I’ve attempted to write this article with minimal bias, probably… maybe.
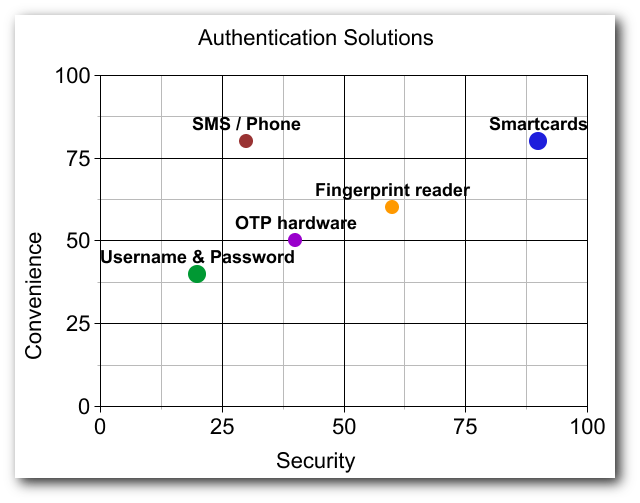
Basically, this brings us down to my top 5 talked about solutions (note: the graph above was not rendered using the latest in authentication solution analysis algorithms, it’s merely a rough layout of where these solutions likely lie relative to each other):
- Username & Password combinations (the classic)
- OTP hardware tokens (RSA SecurID, FortiToken, YubiKey, etc…)
- SMS (access code sent to your mobile device via text message, BattleNet Authenticator)
- Fingerprint Scanner technology (found in consumer laptops/mobile)
- Smartcards (Credit cards, DoD CAC cards, WWPass PassKey)
Usernames & Passwords

The most widely used form of website and services authentication is, by far, using usernames and passwords. They’re hardware free (the user only needs the single factor of “what they know”) and easy to maintain (if you’re only dealing with a small set of them). Unfortunately, this method is usually not well maintained in that many people either write their credentials down somewhere (which is just begging to be taken or looked at by someone else) or they use the same credentials at multiple sites.
Pros
- No additional hardware requirements for the end user
- Free (see the previous point)
- Widely implemented (almost every major website/service on the planet supports it)
Cons
- Quite insecure as it’s only a single factor (something you know)
- Susceptible to brute-force (guessing, dictionary/hybrid attacks)
- Susceptible to screen scraping / keylogging
- A royal pain in the ass to maintain when dealing with more than a handful of username/password pairs
Additional reading
- http://www.cbsnews.com/news/the-25-most-common-passwords-of-2013/
- http://money.cnn.com/2013/12/04/technology/security/passwords-stolen/
OTP tokens

These hardware OTP USB devices generate a One Time Password every X amount of seconds resulting in a one-time use, time sensitive, access code. These depend on having a rock solid random number generator (RNG) or OTP synchronization in order to prevent hackers from predicting the time-based output. The basic (native) user experience is as follows: the user browses to the desired authentication-requiring website and is then prompted to enter the correct access code. The user would then pick up the associated OTP hardware token, read the code displayed, and enter that code into the website’s prompt and, if the code is still valid within the time allotted, the user is granted access.
Another scenario is that the user uses the tokens as a credentials store. This enables a wider range of applications to support the OTP device by allowing the user to house traditional usernames and passwords within the OTP device itself (guarded by the OTP code). Certain password management software allow the use of OTP devices this way so a user can still keep track of their existing usernames and passwords but leverage the OTP token’s security model.
Some OTP devices are application specific (one OTP device for one specific website/app) and this is, in my opinion, a really poor model to work with. If you have an AOL, BattleNet, <insert app here> authenticator then you’re kind of in the same boat as having to remember usernames and passwords for multiple sites. Not all OTP solutions are like this, just note that they exist.
Pros
- No software requirements (hardware has built-in display)
- Some major websites and SSO implementations support OTP
- Single authentication code, no multiple credentials to remember
Cons
- Purchase of a hardware OTP token (usually in the $20-$60 range)
- Popular OTP solutions have been hacked in major ways (search for RSA SecurID hacked articles)
- No hardware tamper proofing
- “All eggs in one basket” risks when using these devices as a usernames and passwords store (compromise of the device would lead to compromises of all contained credentials)
- The time-sensitive nature can be annoying if you catch the device at the wrong time (right before changing codes)
- Vendor lock (usually requires specific drivers/software from the manufacturer)
- Possible server/client synchronization issues (but I personally have never encountered this problem)
Additional reading
- http://www.youtube.com/watch?v=kXB0BwwvZ1E
- http://arstechnica.com/security/2012/06/securid-crypto-attack-steals-keys/
Mobile SMS
SMS software token authentication typically acts just like OTP hardware tokens, minus the additional hardware (assuming you have a smartphone already). The user goes to some website or service and requests access to something. The website tells the user to enter the OTP from their authenticator app and the user opens the (usually) service-specific authenticator app on their phone to get the time-sensitive code. Some solutions do not rely on applications to be installed on the user’s phone and instead opt to send an OTP via text message (SMS).
Pros
- No software or hardware requirements (requires existing phone/smartphone)
- Some major websites and SSO implementations support OTP
- Single authentication code, no multiple credentials to remember
- Mostly vendor independent (most smartphones will support an auth app)
Cons
- SMS/GSM is not considered very secure
- Your phone is typically protected by weak security and thus could be taken and used to then access systems requiring SMS-based OTP
- Popular OTP solutions have been hacked in major ways (search for RSA SecurID hacked articles)
- No hardware tamper proofing
- “All eggs in one basket” risks when using these devices as a usernames and passwords store (compromise of the device would lead to compromises of all contained credentials)
- The time-sensitive nature can be annoying if you catch the device at the wrong time (right before changing codes)
Additional reading
- http://hackaday.com/2013/10/22/cracking-gsm-with-rtl-sdr-for-thirty-dollars/
- http://www.pcworld.com/article/2079620/banks-shouldnt-rely-on-mobile-sms-passcodes-security-firm-says.html
Fingerprint Scanner
A growing trend in the consumer laptop market is the addition of fingerprint scanners (biometrics). Biometrics have long been thought of as the “perfect” solution to proving one’s identity, but there are still a few catches. Firstly, when you read about biometrics research pay close attention to what kind of biometrics are being used as well as the method of using it (lengthy many-point verification with additional measures such as infrared blood flow detection or few-point fingerprint scanning, for instance). With the integration of fingerprint scanners into laptops and phones, it provides users quick access to their device (logon process integration) without requiring any additional hardware or software (usually). It’s also really hard to forget your finger, so that helps too…
Pros
- No software or hardware requirements (requires existing phone/smartphone/laptop)
- External readers available for purchase if no existing compatible device exists
- Device OS logon integration (use your fingerprint to log into your device)
- Multiple applications can/could leverage fingerprints as a way to access information (encrypted data, websites, etc…)
Cons
- Not widely supported beyond manufacturer-specific applications and OS access
- Good security but, depending on the implementation, not great security
- Platform dependent (can’t go from device to device with much ease or consistency).
- I’d be worried for my finger’s safety in an extortion attempt
- Vendor lock (usually requires specific drivers/software from the manufacturer)
Additional reading:
- http://computer.howstuffworks.com/fingerprint-scanner5.htm
- http://www.youtube.com/watch?v=geTgSzrKYdc (fixed now)
Smartcards
Smartcards are built around the Secure Element (Secure Cryptoprocessor) technology which can be found in Passports, Credit Cards, USB authentication tokens, and more. Secure cryptoprocessors are unlike some of the other previously discussed technologies in that they are, themselves, a secure platform and do not rely on another platform to perform essential tasks such as random number generation (which, if done incorrectly or using poor algorithms, can lead to the prediction of those numbers and ultimately a vector to crack the system as a whole).
Instead of the authentication device providing a private key to another platform/OS for encrypting/signing data, the data is given to the smartcard first, it’s encrypted/signed within the trusted platform (private keys are never exposed), and the encrypted/signed data is outputted. There are also some neat perks of these smartcards such as hardware tamper proofing.
Some smartcards even leverage secure cloud storage for authentication material for those seeking maximum security and control. The WWPass PassKey is a new take on this technology called Smartcard in the Cloud and brings serious security and convenience to the consumer market. Available in USB+NFC formats, it provides easy connectivity to devices over a wireless medium. So cloud, such security, many wow!
Pros
- Widespread support in major desktop OS’s (Windows, Mac, Linux)
- Device OS logon integration (use your smartcard to log into your device)
- Multiple applications can/could leverage smartcards as a way to access information (encrypted data, websites, etc…)
- Hardware tamper proofing
- Self-contained secure platform (more guarantee the bad-guys can’t predict output or access the private key)
- Extremely versatile Java Card tech (encrypt/sign data, store credentials, basic auth)
- PKI (public key / certificates) support
Cons
- Great security but can be slow (depending on implementation)
- Popular mobile devices do not have Secure Cryptoprocessors on-board and require additional purchase
- More expensive than the simpler OTP hardware
- Vendor lock (usually requires specific drivers/software from the manufacturer)
Additional reading