Untangle website: http://www.untangle.com/
VMware website: http://www.vmware.com/
So you have a few VMware VM’s acting as web servers or OpenVPN or whatever… Now you want them protected by a firewall or to have their own subnet equipped with a DNS or DHCP server or maybe subnet gateway anti-virus.
It’s actually pretty easy to force VMs to send their traffic through another VM. In this case we’ll be using Untangle as the router VM and an Ubuntu Server as the protected VM on the same ESXi host. The basic principal is to create two vSwitch instances; an outside network and an internal network. We’re not using multiple NICs here so the “internal” network refers to a network that only VMs within the host can access.
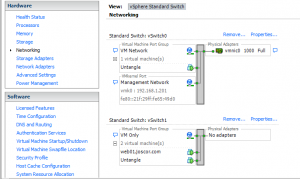
To start, we need to create a new vSwitch that’s not connected to a physical network adapter (NIC). The image below shows a configured sample model. Basically there’s the router (Untangle) with one NIC facing the public (connected to vSwitch0) and one internal VM Only NIC (connected to vSwitch1). Then there’s the test VM server which is only connected to the internal vSwich1 network. With this setup the test VM (web01) will be able to receive DHCP from the Untangle VM and use it as its gateway, then the Untangle VM can pass through traffic to the public network whilst monitoring and sanitizing the connection to and from the internal VMs.
The logic behind this is pretty simple after it sinks in. Basically think of vSwitches as real switches. Here we have vSwitch1 with two devices plugged into it; Untangle and the web01 server. Since web01 is configured to use Untangle as the gateway device, Untangle receives packets using it’s “internal” NIC and then send its through it’s “external” NIC which here is connected to vSwitch0 (and thus, out through the physical NIC).
This model can be implemented a few different ways. One way is to use the “Router” as a subnet router which gives it mostly a firewall role (which is portrayed above). In this method there will be a master gateway router which this router VM would connect to. The advantage here is that only the VMs are protected and that only one physical NIC is needed (as the “router” is only protecting internal VMs which are virtually connected).
The other method would be to use two NICs, once for the real public network (connected to a modem) and one for the real physical internal network (connected to a wireless AP or physical switch) and then still have the virtual “VM Only” vSwitch. The advantage here is that the virtual router would then be protecting all systems behind the modem (physical and virtual).