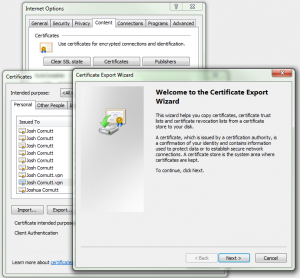
If you have a PKI certificate in your Windows PC that you would like to use to log in to your OpenSSH-enabled Linux server, it can be a pain to figure out how to extract the public key from this file and convert it into a format OpenSSH can understand. To start with, we need to find the certificate to use, which is located in the Microsoft Certificate Store. A quick and dirty way to see your certificates is to go into Internet Explorer, find the Internet Options, go to the Content tab, and click on Certificates. Once you locate the certificate you want to use to log in to your OpenSSH server, select it and click the Export… button at the bottom of the Certificates dialog box. This will start the Certificate Export Wizard.
Follow the options below to complete the wizard.
- Do NOT export the private key
- Format: DER encoded binary X.509 (.CER)
Now that you have an exported public certificate/key pair, you need to copy this file to your Linux system. You can either do a file copy or open the new certificate file in a text editor and copy the text contents and paste them in a new file in the Linux system. Execute the following command in your Linux system to extract just the public key from your DER-encoded certificate:
$ openssl x509 -in joscor.crt -pubkey -noout > joscor.pub.tmp
Now that you have the public key extracted, it needs to be converted into PKCS#8 OpenSSH format (as it’s currently in OpenSSL format).
$ ssh-keygen -f joscor.pub.tmp -i -m PKCS8 > joscor.pub
Now we have a winner! This file now contains the information to place into your .ssh/authorized_keys file to allow users to authenticate into your OpenSSH server. If you need help with this part or if you’re looking to take security to the next step with the WWPass PassKey hardware token, please refer to the following article: Securing OpenSSH with WWPass PassKey