Check out the original text by Joscor’s founder: http://blog.dins-os.com/2013/01/using-wwpass-passkey-security-token.html
Why keep a huge mental list of passwords and keyfile locations when you can have a highly secure physical token encrypt and decrypt files for you? The WWPass PassKey offers true two-factor authentication by first authenticating the physical USB token ID against a distributed authentication network and then also requiring a PIN to unlock the application-specific “container” where you will find the Truecrypt keyfile.
On a personal note, I work for WWPass and I don’t want to give a wrong impression. I wouldn’t write about a product that I didn’t really like and I personally find pairing Truecrypt and WWPass PassKey to be a very beneficial during my daily routine. It saves me time and headache and lets me sleep well at night knowing my files are more secure than ever.
The beauty of the WWPass PassKey is that the Truecrypt key file, which should be protected above all else, is stored in an encrypted and fragmented state across multiple geographically diverse data centers. I believe their current infrastructure can sustain up to 3 or 4 entire data center security compromises before any possibility of data reconstruction can happen. WWPass themselves can’t access user data and can’t even tell which sections of storage correspond to any user. They offer pure anonymity for storage and authentication.
OK, now back to the how-to part of this how-to.
1) Before you can use the WWPass PassKey you must download the WWPass Security Pack from their website (wwpass.com). By installing this pack you will also have installed the WWPass Cryptoki PKCS#11 library. This library tells Windows how to treat the cryptographic device.
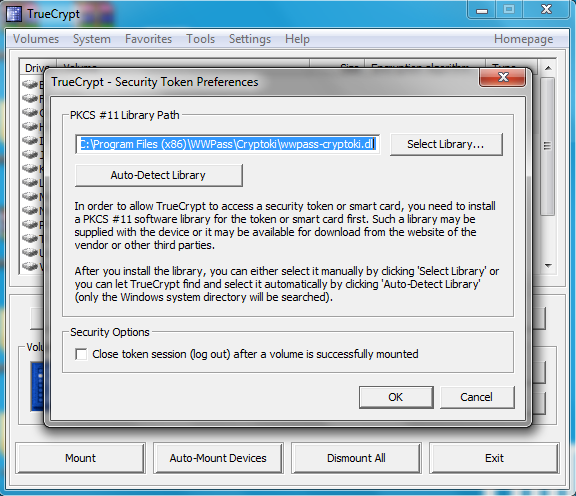
2) Now we need to tell Truecrypt to use the PKCS#11 library. In the Truecrypt GUI click on “Settings->Security Tokens…”. Click OK to get past the info pop-up and you should be greeted with a browser file selection box. Unless you’ve installed the WWPass Security Pack in an odd place, you should be able to find the library at “C:\Program Files (x86)\WWPass\Cryptoki\wwpass-cryptoki.dll”.
3) Now that Truecrypt can see your PassKey USB token, it’s time to generate a Truecrypt keyfile (if you don’t already have one). Click on “Tools->Keyfile Generator” and in the next dialog box pick your hashing/key poison, then generate and save the file to disk (temporarily).
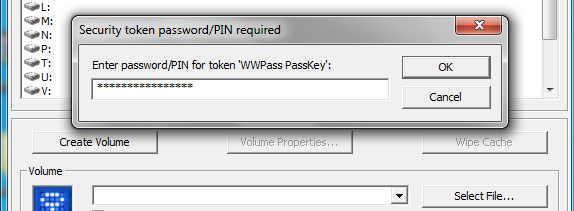
4) We need to then get the newly generate Truecrypt keyfile onto the USB token’s “storage” (remember, the token itself has no real storage, the “storage” referred to here is actually an encrypted distributed data storage). To do this, click “Tools->Manage Security Token Keyfiles” and enter your PIN/PassCode. Select, at the bottom, “Import Keyfile to Token” and then select your previously generated keyfile.
5) Lets give it a test, shall we? Create a new container and when it asks for a container password/keyfile, check the “Use keyfiles” box and then click on the “Keyfiles…” button. Now click the “Add Token Files…” button. Once again enter your WWPass PIN/PassCode to gain access to your distributed secure token data. You should now see a list of any keyfiles which you have previously imported. Select the one you want and you have now used your PassKey to secure files using Truecrypt! Physical token control, distributed encrypted secure storage, and high security keys for encryption. I dig it!
6) … aaaaand presto! You now have a securely stored Truecrypt keyfile which you can now use to encrypt and decrypt containers and other secure storage mediums containing questionable contents.